Boiling the egg
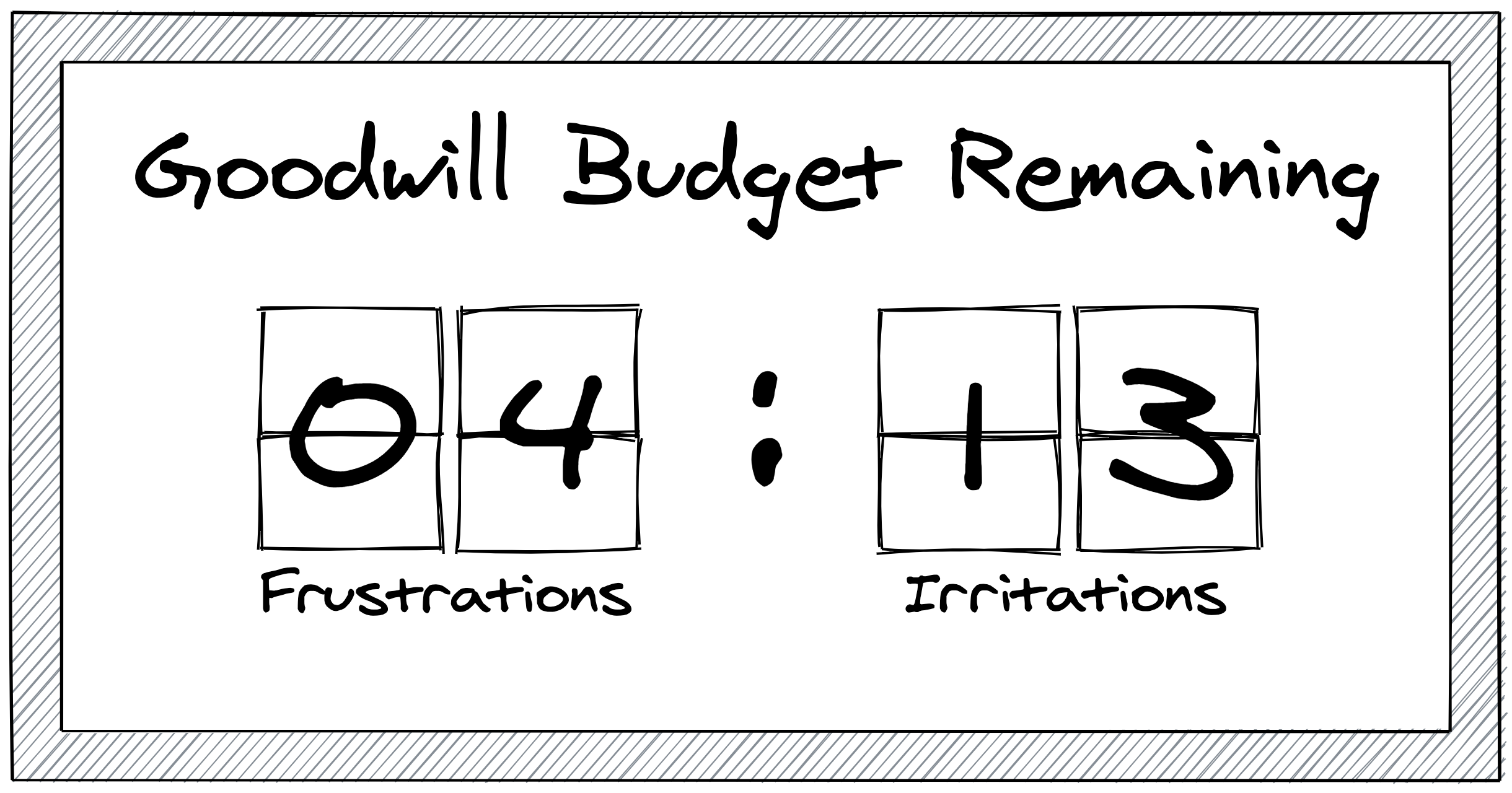
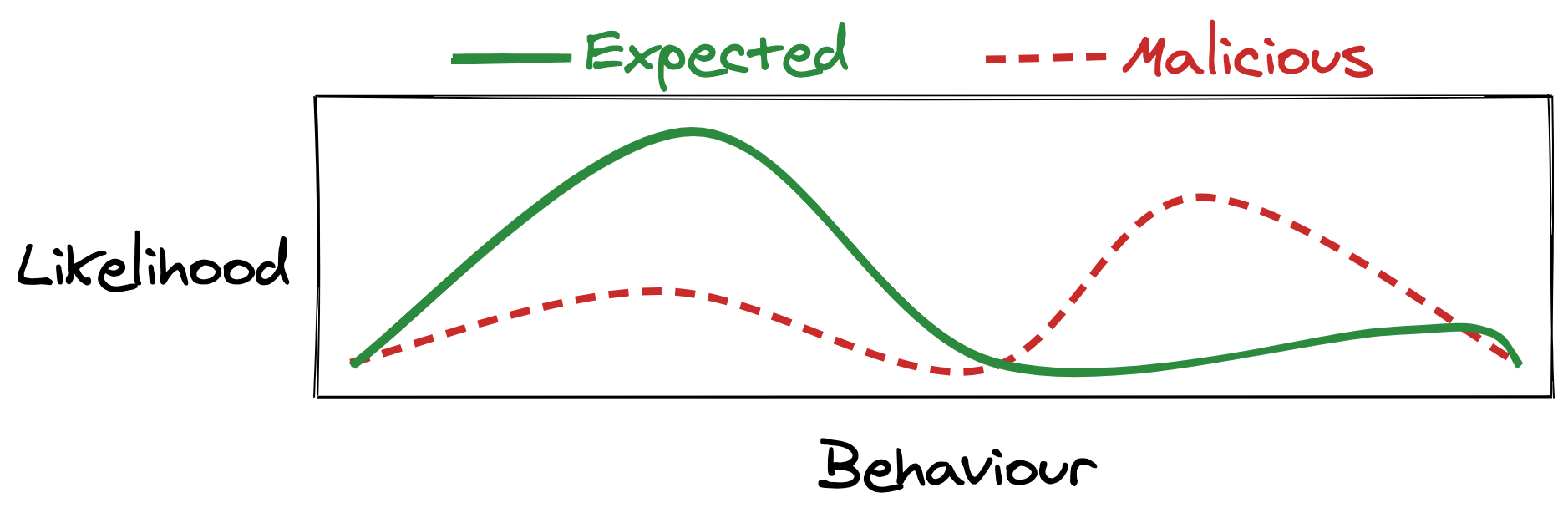
If you compromise an employee at a mature, well-secured enterprise, what do you get? Lots of team-specific communication and documents, sure, but any broader company information or systems access is usually locked down behind approvals processes. Getting to anything good requires some lateral movement and privilege escalation.
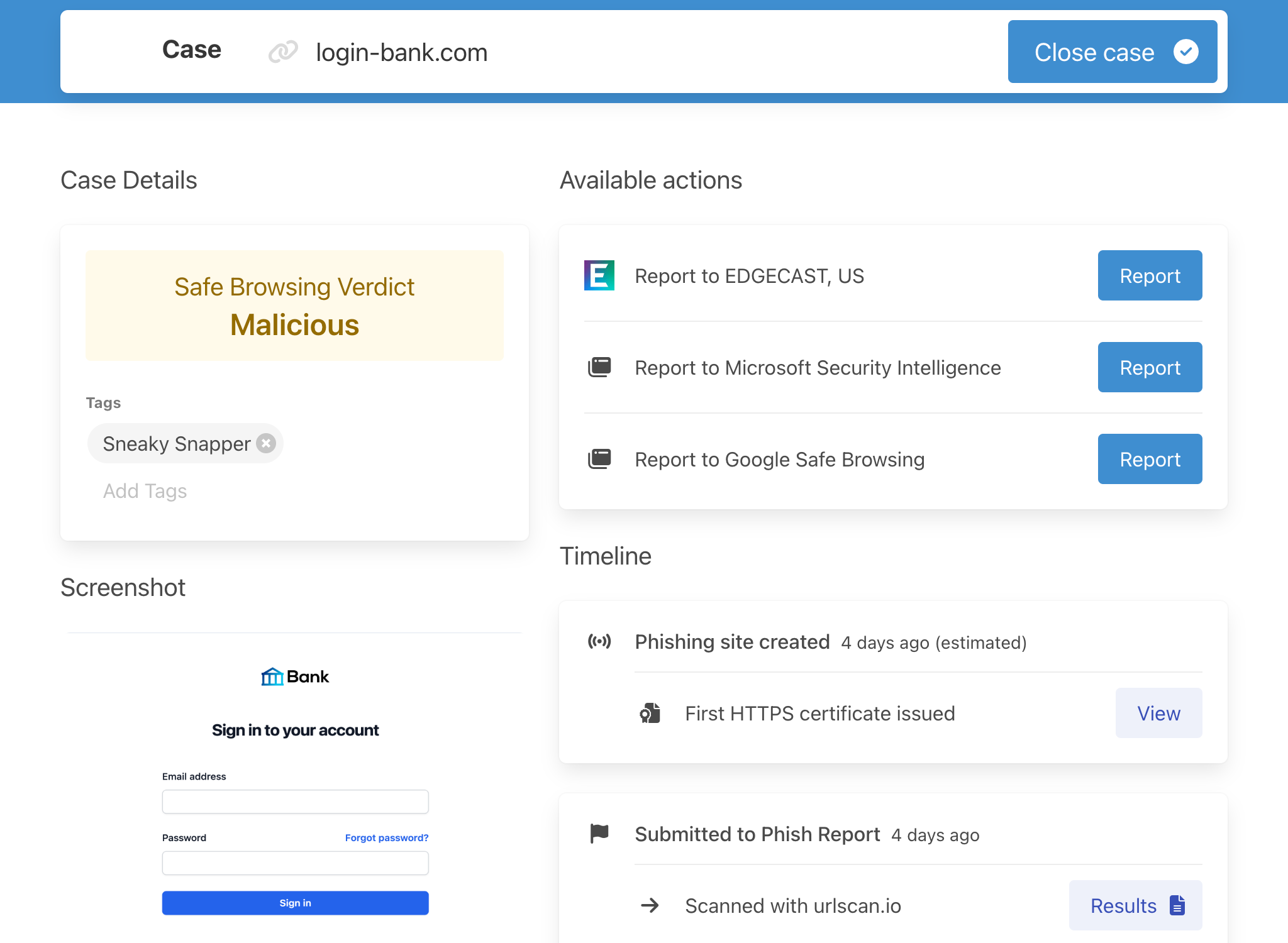
Startups, however, are like a raw egg. Break the shell, and everything falls out:
- A huge chunk of their Slack instance: company conversations and every embarrassing detail from the #incidents channel.
- Broad access to production systems and data.
No extra work required.